Wide
1
We've received reports that Draeger has stashed a huge arsenal in the pocket dimension Flaggle Alpha. You've managed to smuggle a discarded access terminal to the Widely Inflated Dimension Editor from his headquarters, but the entry for the dimension has been encrypted. Can you make it inside and take control?
The above is the description for a Hack The Box challenge titled “WIDE.” The description instructs me to a “dimension” however it is encrypted. Downloading the challenge files there are two items in the zip folder wide and db.exe.
wide is a Linux ELF binary
1
2
3
┌──(root㉿kali)-[~/htb/challenges/crypto/wide]
└─# file wide
wide: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=13869bb7ce2c22f474b95ba21c9d7e9ff74ecc3f, not stripped
db.ex is a Matlab file according to file, I’ve never heard of this type of file before.
1
2
3
4
5
6
7
8
┌──(root㉿kali)-[~/htb/challenges/crypto/wide]
└─# file db.ex
db.ex: Matlab v4 mat-file (little endian) , numeric, rows 1835627088, columns 29557
┌──(root㉿kali)-[~/htb/challenges/crypto/wide]
└─# cat db.ex
Primuspeople breathe variety practiceOur home dimensionCheagazscene control river importanceThe Ice DimensionByenooviafighting cast it parallelThe Berserk DimensionClotepreafacing motor unusual heavyThe Hungry DimensionMaraqastomach motion sale valuableThe Water DimensionAidorfeathers stream sides gateThe Bone DimensionFlaggle Alphaadmin secret power hiddenHOt*{Xt0ANe
Running the binary with the db.ex file gives a menu of the “Widely Inflated Dimension Editor.” Pressing 1,2,3,4, etc on the keyboard will select the respective Dimension.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(root㉿kali)-[~/htb/challenges/crypto/wide]
└─# ./wide db.ex
[*] Welcome user: kr4eq4L2$12xb, to the Widely Inflated Dimension Editor [*]
[*] Serving your pocket dimension storage needs since 14,012.5 B [*]
[*] Displaying Dimensions.... [*]
[*] Name | Code | Encrypted [*]
[X] Primus | people breathe variety practice | [*]
[X] Cheagaz | scene control river importance | [*]
[X] Byenoovia | fighting cast it parallel | [*]
[X] Cloteprea | facing motor unusual heavy | [*]
[X] Maraqa | stomach motion sale valuable | [*]
[X] Aidor | feathers stream sides gate | [*]
[X] Flaggle Alpha | admin secret power hidden | * [*]
Which dimension would you like to examine?
Flaggle Alpha (#6) is encrypted and probably contains the flag for this challenge.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(root㉿kali)-[~/htb/challenges/crypto/wide]
└─# ./wide db.ex
[*] Welcome user: kr4eq4L2$12xb, to the Widely Inflated Dimension Editor [*]
[*] Serving your pocket dimension storage needs since 14,012.5 B [*]
[*] Displaying Dimensions.... [*]
[*] Name | Code | Encrypted [*]
[X] Primus | people breathe variety practice | [*]
[X] Cheagaz | scene control river importance | [*]
[X] Byenoovia | fighting cast it parallel | [*]
[X] Cloteprea | facing motor unusual heavy | [*]
[X] Maraqa | stomach motion sale valuable | [*]
[X] Aidor | feathers stream sides gate | [*]
[X] Flaggle Alpha | admin secret power hidden | * [*]
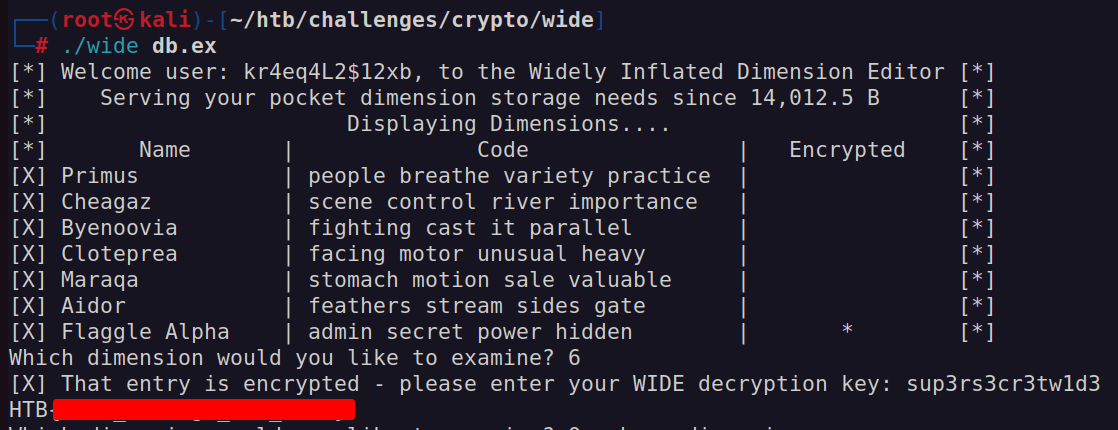
Which dimension would you like to examine? 6
[X] That entry is encrypted - please enter your WIDE decryption key: key
[X] Key was incorrect [X]
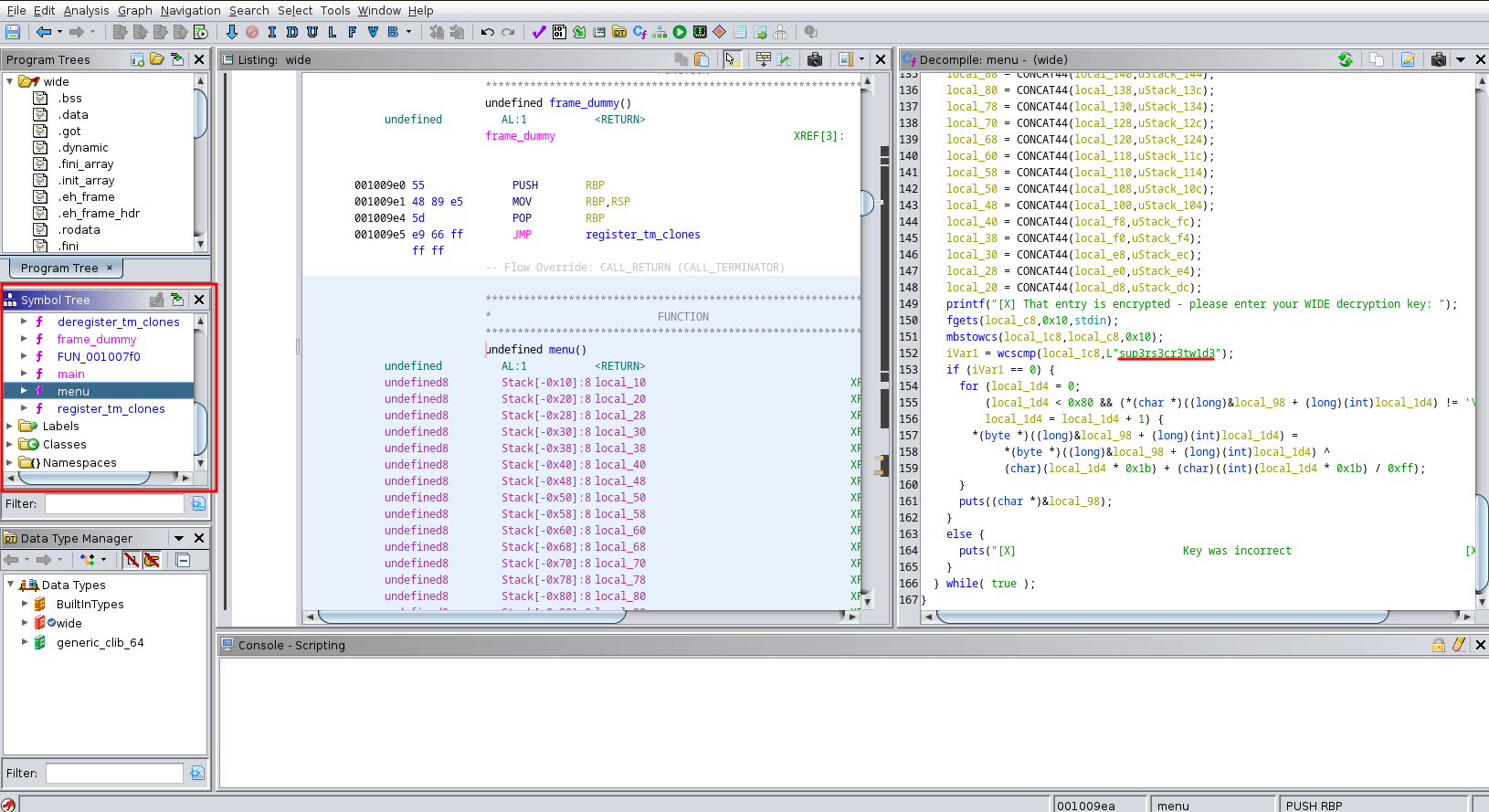
I opened up ghidra and imported the wide binary. ghidra was able to identify a function called menu and looking at the code there I found a hard-coded password. sup3rs3cr3tw1d3